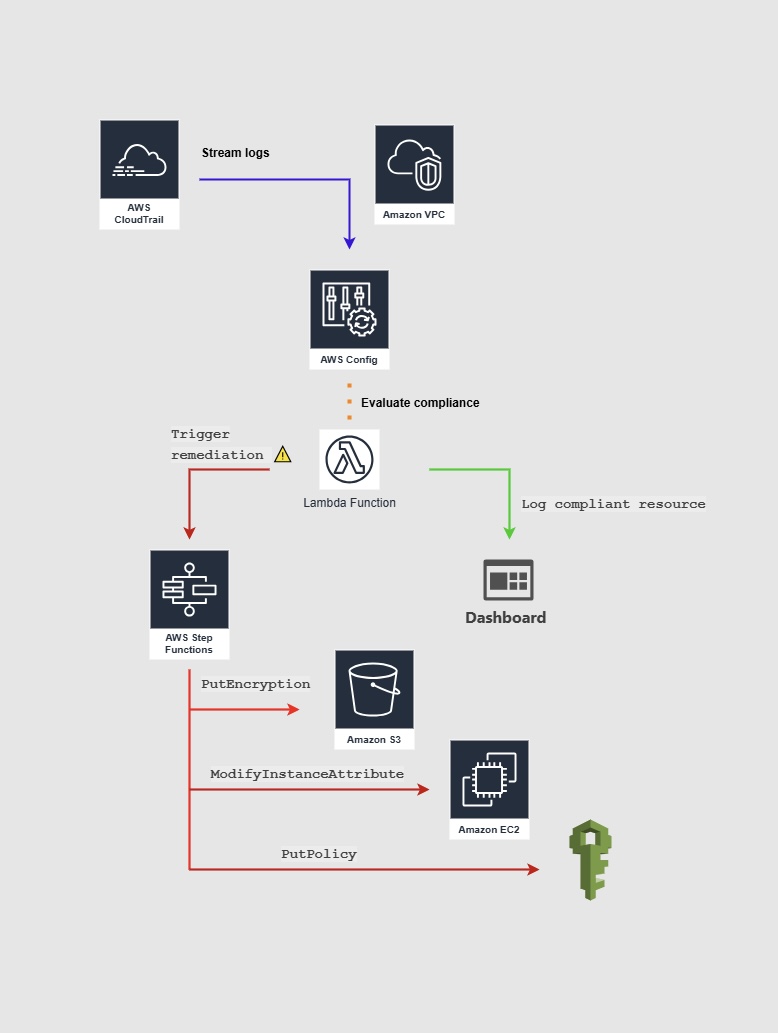
Compliance Automation Architecture
Implementation Details
The framework was built using AWS Config, Lambda, and Step Functions, with the following workflow:
1. CloudTrail/VPC Flow Logs
Raw data sources tracking all API calls and network traffic:
- Example Event:
s3:PutBucketPolicyAPI call - Security Check: SSH attempt from unexpected IP (
203.0.113.42)
2. AWS Config Rules
Predefined and custom rules for compliance evaluation:
def evaluate_compliance(config_item):
# Check if EC2 has termination protection
if config_item['resourceType'] == 'AWS::EC2::Instance':
return config_item['configuration']['disableApiTermination']
return 'NON_COMPLIANT'3. Lambda Evaluator
Custom business logic processing:
if event['configRuleName'] == 's3-encryption-check':
if bucket_config['ServerSideEncryption'] == 'AES256':
return 'COMPLIANT'
trigger_remediation()4. Remediation Workflow
Step Functions state machine handles complex fixes:
- Auto-enable S3 bucket encryption
- Revoke permissive IAM policies
- Isolate non-compliant resources